Reversing Hyperion's Deleter2 Mechanism
WARNING:
The following blog is a stub and isn’t finished due to me being occupied.
I have left the rest of the writing over to Atrexus to handle, but for now all of this is written and reversed by me, Atrexus will simply document and finish the blog in my favor.
Introduction
Hello everyone, I am back once again with another very good read for you. This one will be talking about the Deleter2 routines of Roblox which are made to detect out of sync memory access with critical game structures. I highly suggest you read this post, even if you don’t care about cheating as it shows a lot of cool mechanisms Hyperion uses internally. Due to all the things I must explain, this will be quite lengthy and a harder read for those newer to reverse engineering. I will try to be as specific as possible, hence the length and explain everything a beginner needs to know to understanding Deleter2 internally. I hope you enjoy this read and take the time to understand everything I say even if it requires re-reading. Unlike the many other posts about Hyperion’s Deleter2 mine will actually be going in depth and directly talking about what happens. Nothing theoretical, but purely an exact reversal of what they do. We will be analyzing 3 different bypasses I have made for Deleter2, which all work differently and have very interesting mechanisms.
Credits
All the work was created by me, (Fish-Sticks / Fishy / Birdy). You can contact me on Discord @ goatthegb. Please don’t ask me to fix your cheat. I’ll help you learn and reverse engineer, but I won’t fix your problems for you, and I may come off very rude but remember it’s nothing personal. Many asked me questions about Serenity which my blog had already answered, please make sure you read carefully before asking for help.
Credits to my communities for supporting me, and making learning computer science a great experience.
Background Knowledge
Windows Paging
To understand Deleter2 we must first understand how Windows manages process memory. Please note while I explain this that I am keeping things relatively simple and the actual mechanisms are more complex and involved than this. If you would like an in depth blog on paging please refer to the resources at the end of this read. When you access a page inside Windows a couple things happen depending on what is at that memory address. When you access a page that isn’t already in memory, the CPU injects a page fault exception. This exception tells Windows that we tried to access an invalid memory address. Now as Windows is our operating system, it sees that we wanted to allocate some memory at that memory address through the VAD. The VAD is Windows’s high level way of managing memory and describing memory regions. Windows will see that we wanted to access our allocated memory, and then it loads it into RAM for us to access. Now when this page isn’t getting accessed Windows has a couple options. They can page it out to disk, to make more room inside our RAM for other important processes, or they can free the memory. If the process needs to still retain the memory but it’s just not being used at the moment, then obviously paging out sounds a lot better of an option as opposed to having to delete and reallocate memory every time. If Windows sees that the address you tried to access isn’t actually an allocated memory region or described then it will simply forward the exception to the usermode exception handlers as an invalid memory access.
Hyperion’s Forced Exceptions
Hyperion has a lot of exception oriented code which is used for signaling events such as intialization. For example, if Hyperion calls the function 0xFFFFFFFFFFFFFFF4 with the first argument being a pointer to a data structure then an invalid memory access will occur and Windows will send an exception to Hyperion’s exception handler, which will check the exception record to see what address was accessed and from where. If it sees that the exception occured from RobloxPlayerBeta.exe and they tried executing 0xFFFFFFFFFFFFFFF4 then they are calling one of Hyperion’s exception events. Hyperion will set the RIP of the _CONTEXT to their function, and then resume execution of the thread, resulting in an indirect function call to a Hyperion handler. This is actually how Hyperion initializes Deleter2 and is our first clue to weakness. These forced exception handlers run the same as a normal exception handler, so there isn’t much to talk about as MSDN already defines everything. All you need to know is that they only allow the PE file RobloxPlayerBeta.exe to access these functions, and if you try to force the exception from any other originating address outside the game module you will simply crash.
Hyperion’s Pointer Encryption
Hyperion has a relatively simple pointer encryption which is used absolutely everywhere and is just another way to make your decompilations look like garbage. Along with this they have dead stores, and opaque predicates. The blog listed in resources does a great job explaining what they mean, and below is an image of the Hyperion pointer encryption (keep in mind the math changes every update).
Deleter2’s Target Audience
Deleter2 is one of Hyperion’s relatively weaker checks and it’s mainly aimed at stopping ESP/Aimbot hacks, or anything with frequent fast reading/writing. Deleter2 doesn’t typically affect internal cheats because they are usually on the game’s engine scheduler which keeps you in sync with the pipeline meaning any reads and writes you do will already be in sync. Thus, external cheats with frequent memory access are what Deleter2 is aimed towards stopping, and it does so quite well for the unexperienced cheater.
Reverse Engineering Deleter2
Deleter2’s Initialization Routine
Now that we understand the core features of Windows that are required to learn about Deleter2 we can get on with the reversal. To start we will be analyzing an instance Deleter2 protects. This instance is commonly used by ESP cheats to retrieve player information such as names and positions. It is called RBX::Humanoid, and you can read about it on the documentation. To figure out how Deleter2 is made we must first understand how it is intialized. The following code snippet below shows the creation of RBX::Humanoid.
// Static variable which allocates guarded memory inside Hyperion
CreateGuardedPointer = (unsigned int(__fastcall*)(int*, int))::CreateGuardedPointer;
if ( !::CreateGuardedPointer ) // Is guarded pointer setup?
{
// Tell Hyperion to setup Deleter2 info
CreateDeleter2StructInfo();
// Creates a guarded page RobloxPlayerBeta.dll + 0x015DE8A0
CreateGuardedPointer = (unsigned int (__fastcall*)(int*, int))::CreateGuardedPointer;
}
// Output pointer for new memory
thisPtr = 0i64;
// Creates a guarded pointer inside Hyperion.
if ( CreateGuardedPointer && !CreateGuardedPointer(&thisPtr, 0xD08i64) )
{
// Fills memory inside the newly allocated memory.
PlayerObje = ConstructPlayer(thisPtr, a2);
}
Although this may seem confusing let’s break down what this code is really doing. We can see that it is checking a static variable which holds the address of a function (we know this because it calls the variable). We can see if this pointer is empty then it calls a function named CreateDeleter2StructInfo, and then sets the guarded pointer variable again. From this we can infer that function must be doing some sort of intialization to fill the pointer. Next we can see it calls CreateGuardedPointer and expects a return value of 0, which we can assume indicates a success. If this occurs we can see it will call ConstructPlayer which is a function that simply populates a pointer with information.
As you can see we have a pointer which gets populated, and returned from the constructor of RBX::Humanoid so we know this pointer IS the humanoid. We can see that the main interest is inside this function which seems to take a variable, populate it with memory, and return a status code with 0 being success.
CreateGuardedPointer(&thisPtr, 0xD08i64)
Since this is more than likely an allocator, we can infer that 0xD08 is the size of RBX::Humanoid, which I can tell you from experience that it is. This gives us a clue as to where to look to understand Deleter2, we must obviously decompile this function and see how it works.
Upon decompiling this function we are presented with a nice surprise from Hyperion. There is an invalid memory call, which passes a static variable which isn’t CreateGuardedPointer and returns the result.
__int64 CreateDeleter2StructInfo()
{
return MEMORY[0xFFFFFFFFFFFFFFF4](&HumanoidDeleterStruct);
}
This may seem like an unrelated variable for the unexperienced reverse but keep in mind that pointers have the ability to represent many different values, and one of them being structures.
Upon looking closer at the address of the static variables we can see something interesting.
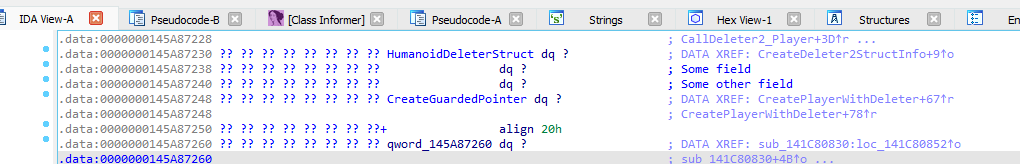 We can see that this function is actually initializing a structure of variables which seem to hold information related to Deleter2. Now the question remains on how we can actually get the real function it’s calling. One way we could do this is by debugging Hyperion and seeing where it goes, but as we know Hyperion has an anti-debug so this option is only available to those who have bypassed it.
Another option remains where we find their exception handler and figure out where this gets handled, and that’s what I’ve done. This is probably the trickiest part for those unexperienced, and I’ll leave you to figuring it out.
We can see that this function is actually initializing a structure of variables which seem to hold information related to Deleter2. Now the question remains on how we can actually get the real function it’s calling. One way we could do this is by debugging Hyperion and seeing where it goes, but as we know Hyperion has an anti-debug so this option is only available to those who have bypassed it.
Another option remains where we find their exception handler and figure out where this gets handled, and that’s what I’ve done. This is probably the trickiest part for those unexperienced, and I’ll leave you to figuring it out.
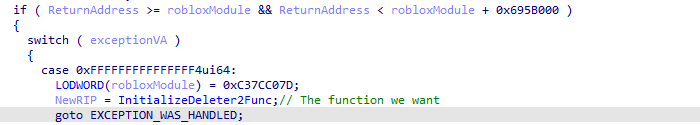
In the picture below shows the end of the function which gets called when RobloxPlayerBeta.exe attempts an instruction fetch on 0xFFFFFFFFFFFFFFF4. This is the function that the CreateDeleter2StructInfo is calling.
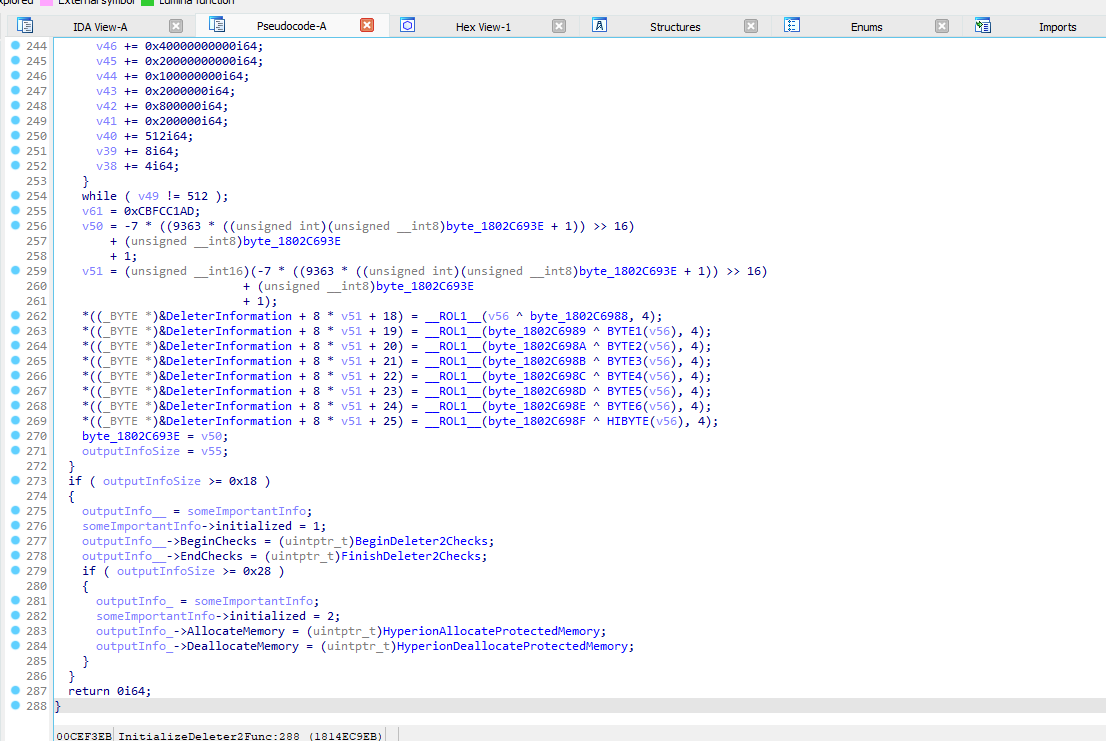 The reason I am showing you the ending is because we only really care about the return value, and the beginning of the function is heavily obfuscated and mostly unrelated code (setting up Deleter2 memory pool) which will bloat this blog.
As you can see I’ve gone ahead and cleaned up the code for you as I’ve already reversed this but we can see that it is filling in the output pointer with 4 different functions. I will explain each of these functions and their purpose after I go ahead an explain to you the Deleter2 pool.
The Deleter2 pool is a special memory pool Hyperion allocates which is reserved for all allocations for protected instances, a couple of those being RBX::Humanoid, RBX::Player, RBX::Players, etc.
This pool is sized at 0x200000 bytes and has custom functions to allocate (reserve) memory inside this pool and deallocate (unreserve). They do not actually allocate and deallocate memory, the pool is always present in memory and takes up all 0x200000 bytes, but rather they simply just call their reservation functions to make room on whatever you want to allocate in it. If you compare the addresses of these protected instances you will notice they are all very close, since they all reside in this pool. This is important to keep in mind, and is another weakness in Hyperion we can exploit.
The reason I am showing you the ending is because we only really care about the return value, and the beginning of the function is heavily obfuscated and mostly unrelated code (setting up Deleter2 memory pool) which will bloat this blog.
As you can see I’ve gone ahead and cleaned up the code for you as I’ve already reversed this but we can see that it is filling in the output pointer with 4 different functions. I will explain each of these functions and their purpose after I go ahead an explain to you the Deleter2 pool.
The Deleter2 pool is a special memory pool Hyperion allocates which is reserved for all allocations for protected instances, a couple of those being RBX::Humanoid, RBX::Player, RBX::Players, etc.
This pool is sized at 0x200000 bytes and has custom functions to allocate (reserve) memory inside this pool and deallocate (unreserve). They do not actually allocate and deallocate memory, the pool is always present in memory and takes up all 0x200000 bytes, but rather they simply just call their reservation functions to make room on whatever you want to allocate in it. If you compare the addresses of these protected instances you will notice they are all very close, since they all reside in this pool. This is important to keep in mind, and is another weakness in Hyperion we can exploit.
HyperionAllocateProtectedMemory: This function is responsible for allocating memory that will be protected by the Deleter2 checks.
// TODO: EXPLAIN THE SETUP OF THE POOL